[ad_1]
One of the most superior Trojans concentrating on banking apps has gotten an improve. Vultur has been wreaking havoc on Androids since safety agency ThreatFabric found it in 2021. According to researchers with NCC Group, the malware has reemerged and is even stealthier than earlier than.
You would possibly keep in mind Vultur for the notoriety it gained for its capability to display report on units remotely. It hid in apps, a few of which have been on the Google Play Store, and contaminated your system.
But now Vultur has new methods to take over Androids and new strategies to trick you into downloading malware. Hackers now make the most of the whole lot from textual content messages to cellphone calls to dupe their victims. Once they get into your system, they’ll take whole management. Hackers can remotely entry and use your cellphone – all in an effort to take your hard-earned cash.

Android cellphone (Kurt “CyberGuy” Knutsson)
Vultur’s new hybrid assault
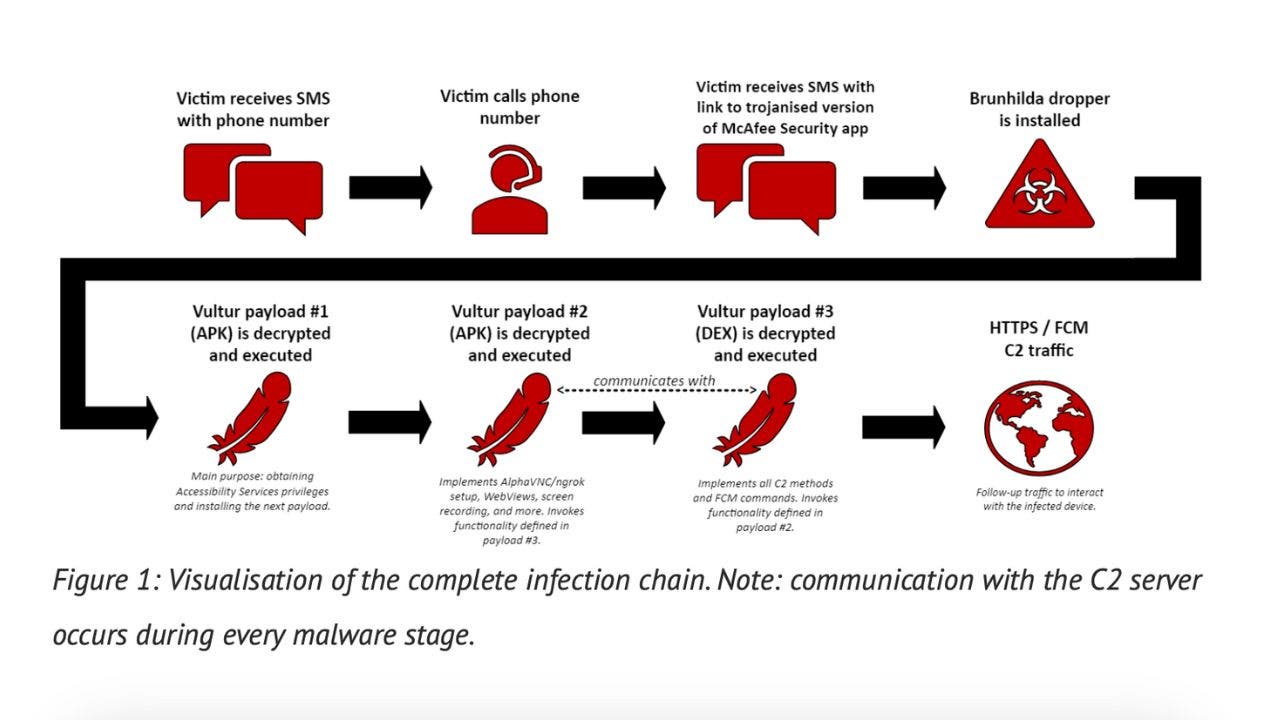
According to NCC Group, this new assault focuses on contacting victims. It begins with a textual content message urging the sufferer to name in the event that they did not authorize a transaction on their checking account. However, the transaction is not actual; it is merely a ruse.
If the sufferer calls, they may obtain directions to obtain a McAfee Security app containing the banking Trojan and a textual content message with the hyperlink.
The safety app seems to be regular however truly incorporates the Brunhilda dropper, a misleading element hidden inside seemingly reputable apps. In this case, the dropper incorporates the Vultur Trojan. It then releases and executes the Trojan in three batches. When the third batch is dropped, hackers can achieve whole management of your Android system.
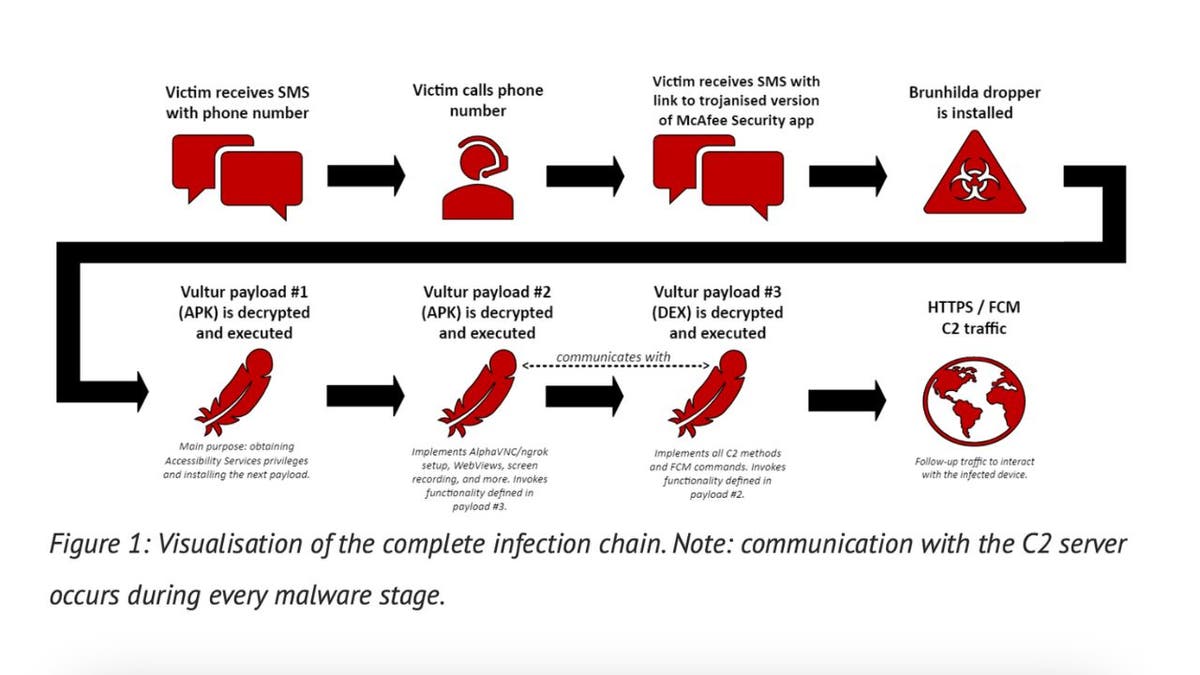
Illustration of an infection chain (NCC Group) (Kurt “CyberGuy” Knutsson)
MORE: HACKERS USE PIRATED SOFTWARE TO HIJACK MAC, ANDROID, WINDOWS DEVICES
Vultur’s new options
Vultur was already a really critical risk to Android customers. But now, that risk has been considerably upgraded due to the stage of management hackers can achieve. Once Vultur has contaminated your system, hackers can set up, delete, add and obtain information. It may even cease apps from working in the first place. If that wasn’t sufficient, Vultur can bypass Android’s Keylock function, bypassing your lock display.
Even extra scary is Vultur’s remote management capabilities. The malware has been in a position to remotely entry units because it was first found in 2021. But now, hackers can instruct the malware to swipe, click on, scroll, mute and unmute audio, and extra, giving them extra management.
Hackers needn’t fear about staying related to the system, both. They have leveraged Google’s Firebase Cloud Messaging system to have the ability to ship directions to contaminated units.

Samsung cellphone (Kurt “CyberGuy” Knutsson)
How to guard your Android from Vultur
One of the greatest methods to remain away from Vultur is to not name after a hacker texts you about approving a big financial institution transaction. You can at all times name your monetary instinct your self to verify. But by no means name an unknown cellphone quantity that is despatched to you by an unknown individual. Here are another suggestions as properly:
Avoid sideloading apps and shortened URLs
Try to not sideload apps. That’s if you set up apps outdoors of a reputable supply. Shortened URLs can mislead customers into downloading malware.
Be cautious granting permissions
Exercise warning when granting app permissions. Consider whether or not an app actually wants entry to sure system capabilities or information.
Limit the apps you’ve on your cellphone
Sometimes, having a whole lot of apps on your cellphone could make it straightforward to be uncovered to malware. These apps can let in malicious code over time, and the extra apps it’s important to hold monitor of and replace, the extra seemingly your Android will probably be weak. Here’s find out how to delete pointless apps from your Android.

Hacker utilizing Android and laptop computer (Kurt “CyberGuy” Knutsson)
MORE: WHAT YOU NEED TO KNOW ABOUT VAJRASPY RAT, THE CYBERESPIONAGE TOOL THAT INFILTRATED GOOGLE PLAY
Download apps from respected sources
Additionally, if you obtain apps, be certain they’re from dependable and bonafide builders. Check critiques and perform a little research earlier than simply hitting “install.”
Keep your Android system up to date
Your cellphone has a means of protecting itself secure with software program and safety updates. Don’t neglect to put in them.
Have good antivirus software program on all your units
Installing antivirus safety on all your units is the greatest method to shield your self from malware. Antivirus software program will forestall you from clicking on doubtlessly malicious hyperlinks which will set up malware on your units, permitting hackers to realize entry to your private info. Get my picks for the greatest 2024 antivirus safety winners for your Windows, Mac, Android & iOS units.
What do you have to do if your information is compromised?
If malware has already invaded your system, then you need to take fast motion to attenuate the harm and safe your system. Here are some steps that you would be able to comply with:
Change your passwords
Vultur can provide hackers entry to the whole lot on your system, together with your on-line accounts and your private or monetary info. To forestall this, you need to change your passwords for all your vital accounts as quickly as attainable. However, you shouldn’t do that on your contaminated system as a result of the hacker would possibly see your new passwords. Instead, you need to use ANOTHER DEVICE, equivalent to your laptop computer or desktop, to alter your passwords. Make certain you employ robust and distinctive passwords which might be tough to guess or break. You may also use a password supervisor to generate and retailer your passwords securely.
Monitor your accounts and transactions
You ought to frequently verify your on-line accounts and transactions for suspicious or unauthorized exercise. If you discover something uncommon, report it to the service supplier or authorities instantly. You must also overview your credit score stories and scores to see indicators of identification theft or fraud.
Use identification theft safety
Hackers can entry the whole lot on your Android system, together with your private and monetary info. They can use this info to create pretend accounts in your title, entry your present accounts and fake to be you on-line. This may cause critical harm to your identification and credit score rating.
To keep away from this, you need to use identification theft safety companies. These companies can monitor your private info, equivalent to your dwelling title, Social Security Number, cellphone quantity and e mail deal with, and notify you in the event that they detect any suspicious exercise. They may also enable you freeze your financial institution and bank card accounts to cease hackers from utilizing them. Read extra of my overview of the greatest identification theft safety companies right here.
Contact your financial institution and bank card firms
If hackers have obtained your financial institution or bank card info, they may use it to make purchases or withdrawals with out your consent. You ought to inform your financial institution and bank card firms of the state of affairs. They may help you freeze or cancel your playing cards, dispute any fraudulent fees and challenge new playing cards for you.
Alert your contacts
If hackers have accessed your e mail or social media accounts, they may use them to ship spam or phishing messages to your contacts. They may additionally impersonate you and ask for cash or private info. You ought to alert your contacts and warn them to not open or reply to any messages from you that appear suspicious or uncommon.
Restore your system to manufacturing unit settings
If you wish to make sure that your system is freed from malware or adware, you’ll be able to restore it to manufacturing unit settings. This will erase all your information and settings and reinstall the unique Android model. Before doing this, you need to again up your vital information and solely restore it from a trusted supply.
Kurt’s key takeaways
Vultur is an extremely subtle banking Trojan with some terrifying options. The incontrovertible fact that hackers can achieve full management of your Android is frightening, making all of it the extra vital that you simply shield your self.
These attacks start with a easy textual content message. It’s as much as you to make the effort to individually name your monetary establishment and see if something’s amiss. Just taking an additional 10 minutes can prevent from having your complete system compromised and your private info uncovered.
How apprehensive are you about Vultur attacks? How do you shield your self from attacks concentrating on your funds? Let us know by writing us at Cyberguy.com/Contact.
For extra of my tech suggestions & safety alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a query or tell us what tales you would like us to cowl.
Answers to the most requested CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
[ad_2]
Source hyperlink