[ad_1]
Trading in cryptocurrency? You may be sitting on a reasonably penny in that digital pockets of yours. Feels nice, would not it? But here is the catch with digital foreign money: Keeping it safe is not a stroll within the park.
Hackers are on the market, working additional time to provide you with new tips to swipe your crypto, doubtlessly emptying your pockets in a single fell swoop. Yep, for these cyber thieves, your digital money is the last word prize. And the worst half? Most of the time, you will not even understand you’ve got been hit till your stability is zero.
Case in level: There’s this contemporary malware on the market, particularly concentrating on macOS, Android and Windows devices. It sneaks in via pirated software, looking to your cryptocurrency to make it its personal. Here’s the way it works.

Woman engaged on a Mac. (Kurt “CyberGuy” Knutsson)
What is the brand new malware concentrating on cryptocurrency customers?
The cybersecurity firm Kaspersky has uncovered a complicated new malware marketing campaign designed to pilfer cryptocurrency from customers’ wallets. This marketing campaign leverages pirated or improperly licensed software as a vector for an infection, exploiting the widespread follow of looking for out “free” variations of paid software on-line.
These cracked purposes, distributed via unauthorized web sites, are embedded with a Trojan-Proxy sort of malware. This malware will not be restricted to simply macOS customers, as latest findings have proven; variants concentrating on Android and Windows platforms have additionally been found, connecting to the identical Command and Control (C&C) server. These variants, like their macOS counterparts, are hid inside cracked software, illustrating the widespread danger throughout completely different working methods.
CHICAGO CHILDREN’S HOSPITAL REGAINS ACCESS TO MEDICAL RECORDS A MONTH AFTER CYBERATTACK
Once the malware is downloaded onto your system, it’s going to instantly begin checking for Bitcoin and Exodus cryptocurrency wallets. If it discovers both one (which could be very unlucky for some customers who’ve each), the malware replaces the pockets and infects it with one other model that is in a position to steal the cryptocurrency. For some individuals, this might quantity to hundreds of {dollars}. And, it is all since you unintentionally downloaded the malware to your macOS, Android and Windows devices.

Woman typing on Mac. (Kurt “CyberGuy” Knutsson))
MORE: HOW CROOKS ARE USING SKIMMERS AND SHIMMERS TO STEAL YOUR MONEY AT YOUR ATM MACHINE
How does this malware get in your system?
Kaspersky reported that this new malware is coming via cracked software purposes on-line. A cracked software has damaged safety, thus making it simpler for hackers to infiltrate it with code. With this, the malware’s creator took pre-compromised variations of the pirated software — one instance being xScope, a paid macOS utility — and altered just a few bytes of code to get the job completed.
Then, in February, safety agency Jamf discovered one other cryptocurrency-focused macOS malware circulating via a pirated model of Apple’s Final Cut Pro software.
Attackers can use this malware to acquire cash or carry out felony actions utilizing your system. It is distributed as .PKG installers, which include scripts that execute after set up, altering system information and organising the malware to run as a system course of.
What pirated purposes are being loaded with this malware?
The pirated purposes are variations of software which were modified to take away or disable options which are solely out there in paid variations, resembling license verification. These purposes are sometimes distributed illegally and with out the consent of the software creator. These are recognized as being loaded with this Trojan-Proxy malware:
GET FOX BUSINESS ON THE GO BY CLICKING HERE
- 4K Image Compressor
- 4K Video Downloader Pro v4.24.3 macOS
- Aiseesoft Mac Data Recovery
- Aiseesoft Mac Video Converter Ultimate
- Allavsoft
- AnyMP4 Android Data Recovery for Mac
- AweCleaner
- Downie 4
- FonePaw Data Recovery
- INet Network Scanner
- MacDroid
- MacX Video Converter Pro
- MouseBoost Pro
- MWeb Pro
- NetShred X
- NetWorker Pro
- Path Finder
- Patternodes
- Perfectly Clear Workbench
- Print to PDF
- Project Office X
- Rocket Typist
- Sketch
- SponsorBlock
- SystemToolkit
- TransData
- Vellum
- VideoDuke
- Wondershare UniConverter 13
- SQLPro Studio
- WinX HD Video Converter for Mac
- Artstudio Pro
- Magic Sort List
- FoneLab Mac Data Retriever
- Apeaksoft Video Converter Ultimate for Mac
Furthermore, the malware marketing campaign extends past macOS, as proven by the truth that Android and Windows platforms are additionally being focused by malware that communicates with the identical command and management server. The purposes or information recognized for these platforms are:
- Android: s276.apk, Swipis_v2.6.1[Mobile].apk
- Windows: wsclient.exe
The lesson is to keep away from downloading pirated software from unauthorized sources to shield your self from such malware infections.

A lady typing on a Mac laptop computer. (Kurt “CyberGuy” Knutsson)
MORE: STEALTHY BACKDOOR MAC MALWARE THAT CAN WIPE OUT YOUR FILES
The misleading ‘Activator’ app and its cryptocurrency heist
When you obtain considered one of these apps, it launches “Activator,” which prompts you to put in your system’s username and password to set up and launch the software, whenever you assume you are putting in an app.
When this occurs efficiently (or, reasonably — unsuccessfully to you), the hacker can spy in your system and obtain instructions from their server. This is when the hacker executes their soiled work: trying to find cryptocurrency wallets, changing them and looting your dough.
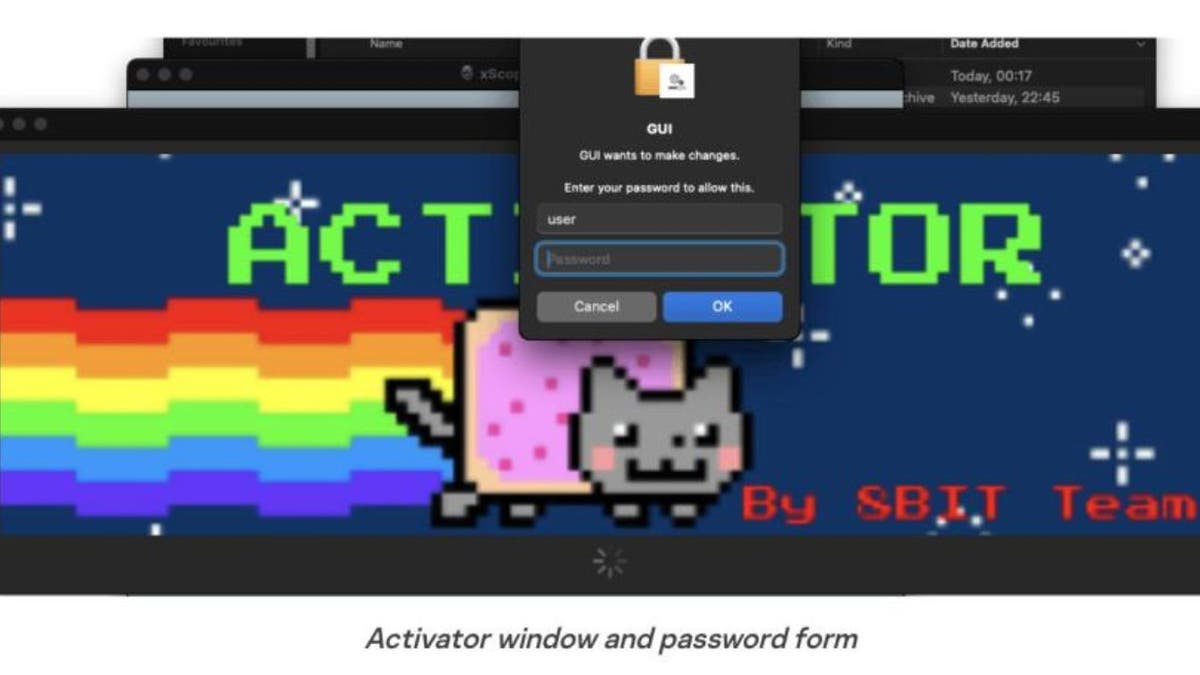
Activator app. (Kurt “CyberGuy” Knutsson)
MORE: BEWARE OF FAKE BROWSER UPDATES ON YOUR MAC
Another be aware that Kaspersky talked about about this specific malware is that it has been concentrating on customers with the macOS Ventura 13.6, which was simply launched in September. We do not know for certain, however this appears to recommend that in the event you’re not operating that, then you definately may be secure from this hack, this time.
Of course, in the event you additionally do not have cryptocurrency, you are most likely okay, too. However, this distinctive sort of malware that makes use of pirated software to get in your system will not be all that new. Hackers have used this methodology of exploiting pirated software earlier than, and they’re going to do it once more.
So, how are you going to preserve your self secure?
Remember, for the hacker to get the malware in your system, you may have to obtain it. This is completed by clicking on a hyperlink or a file that is typically suspicious, however not at all times. In the case of this menace, hackers perceive that cryptocurrency customers are most likely extra tech-savvy than the typical particular person, and are subsequently extra attuned to hacks which are on the market. Because of this, hackers have to discover methods to trick you into downloading the malware within the first place. So listed here are 5 issues you are able to do to shield your self.
1) Don’t obtain bootleg software: It’s not definitely worth the danger to obtain bootleg software. It exposes your system to potential safety threats, resembling viruses and adware. Downloading software from respected app shops is certainly the best way to go to shield your devices.
2) Don’t click on on suspicious hyperlinks or information: If you encounter a hyperlink that appears suspicious, misspelled or unfamiliar, keep away from clicking on it. Instead, think about going immediately to the corporate’s web site by manually typing within the internet deal with or trying to find it in a trusted search engine. Typically, the primary or second end result that seems is reputable.
3) Update your system with software repeatedly: Regularly updating your system’s software is essential for safety as a result of it ensures that you just obtain the most recent patches, bug fixes and safety enhancements. These updates assist shield your system from vulnerabilities and potential threats that could possibly be exploited by malicious actors.
4) Consider storing your cryptocurrency pockets in an exterior onerous drive: If you do have cryptocurrency, you may at all times think about storing your pockets in an exterior onerous drive. This storage methodology signifies that it is secure from hackers on the web.
5) Have good antivirus software: The greatest means to shield your self from clicking malicious hyperlinks that set up malware that will get entry to your personal info is to have antivirus safety put in on all of your devices. This can even warn you of any phishing emails or ransomware scams. Get my picks for the most effective 2024 antivirus safety winners to your Mac, Windows, Android & iOS devices.
Kurt’s key takeaways
A brand new day comes with new malware that’s concentrating on these of you who use Mac, Windows and Android devices and who’ve cryptocurrency wallets. It’s a scary menace that might value you some huge cash in the event you’re not cautious. But you may shield your self by following the steps above, so you may take pleasure in your cryptocurrency with out worrying about dropping it to hackers.
CLICK HERE TO GET THE FOX NEWS APP
Do you imagine authorities rules ought to play a stronger position in defending crypto customers? Let us know by writing us at Cyberguy.com/Contact
For extra of my tech suggestions and safety alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a query or tell us what tales you want us to cowl.
Answers to the most-asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
[ad_2]
Source hyperlink





