[ad_1]
If you use X, previously often called Twitter, you may’ve seen grey or gold-verified accounts selling cryptocurrencies.
They typically pose as precise cryptocurrencies. While you would assume these cryptocurrencies are reliable — in actuality, it is the work of hackers who hijack X accounts.
These hackers goal politicians, corporations and different official accounts that you belief so as to trick you into shopping for into their crypto rip-off.
Some act as middlemen, promoting accounts to malicious actors.
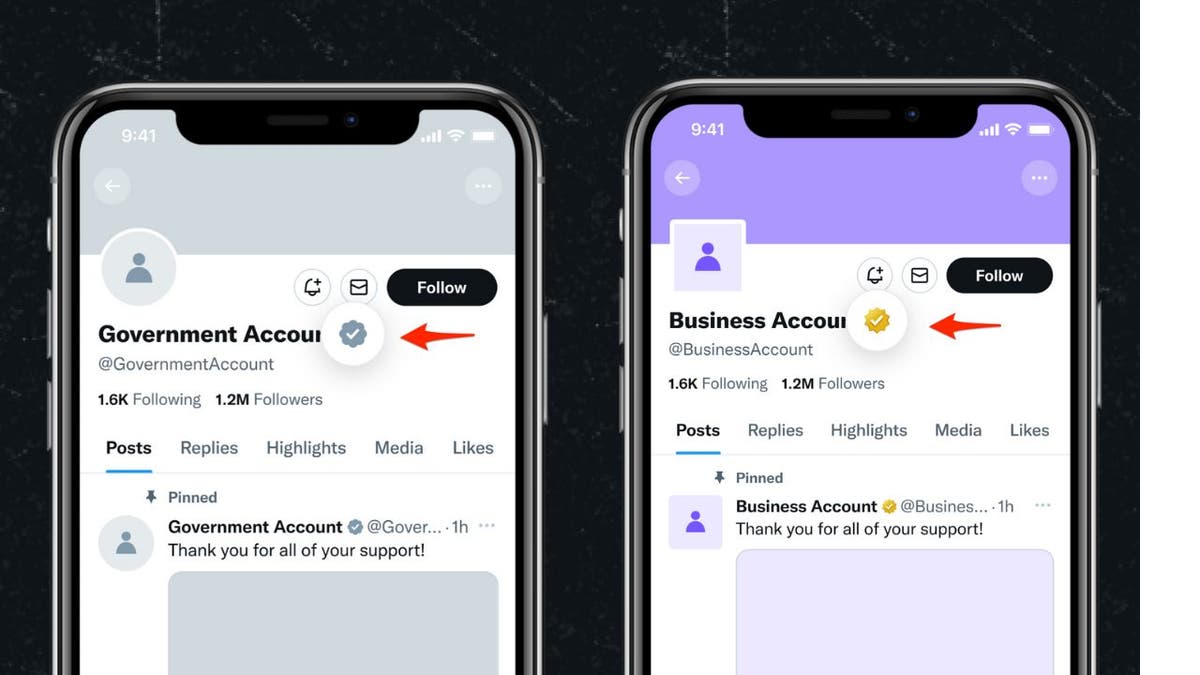
Example of X verified accounts with grey and gold examine marks (X Corp.)
Using trusted accounts for crypto scams
Cybersecurity specialists MalwareHunterTeam discovered accounts belonging to a Canadian senator, a Brazilian politician and a nonprofit all getting used to push cryptocurrencies. According to their stories, hackers used the Canadian politician’s account to pose as a reliable cryptocurrency challenge, whose precise account is not even verified.
FBI’S POST HONORING MLK FLAGGED BY X WITH FACT-CHECKING COMMUNITY NOTE
That assault is two-fold. Not solely are hackers attempting to trick X customers into pondering that they are an precise cryptocurrency challenge, in addition they use that gold or grey examine mark to make you assume they are reliable.
Cybersecurity agency Mandiant additionally had its X profile taken over. Hackers modified the profile to impersonate the Phantom crypto pockets. They then promised free tokens to customers who clicked a hyperlink.

Retweet by a hacker (MalwareHunter Team)
The screenshot above exhibits how the attacker used the official Phantom account to retweet posts that warned customers to “never rush into clicking links.” This was most likely a tactic to make their future crypto rip-off posts look extra credible.
US WATER UTILITIES TARGETED BY FOREIGN HACKERS, PROMPTING CALLS FOR CYBERSECURITY OVERHAUL
However, a BleepingComputer report discovered that customers who clicked on the hyperlink would get redirected to obtain the true Phantom cryptocurrency pockets. That’s when hackers would assault — draining unsuspecting customers’ crypto wallets.

Phantom X account (MalwareHunter Team)
MORE: THE NEW IPHONE SECURITY THREAT THAT ALLOWS HACKERS TO SPY ON YOUR PHONE
How to keep secure on X
Even although these hackers are doing all the pieces they’ll to trick you into giving them your cash, you can take these 10 steps to shield your self.
1. If it is too good to be true, then it most likely is not true
The previous adage is often proper. Most hackers hope you do not see by their schemes and assume that you’re getting an unbelievable deal. However, you have to ask your self: Why would an organization simply give out free cryptocurrency? Wouldn’t there be a catch? What’s in it for the corporate?
2. Do your analysis
Before investing in cryptocurrency, you ought to be certain you have completely seemed into it. Make certain you know what you’re investing in, and you’ve spent ample time researching it. Just clicking on a social media publish and trusting it often is not an awesome thought and might make you a goal for hackers.
3. Use a robust password
Use a robust password that you don’t reuse on different web sites. Consider utilizing a password supervisor to generate and retailer advanced passwords. It will assist you to create distinctive and difficult-to-crack passwords {that a} hacker might by no means guess. Second, it additionally retains monitor of all of your passwords in a single place and fills passwords in for you when you’re logging into an account in order that you by no means have to keep in mind them your self. The fewer passwords you keep in mind, the much less possible you might be to reuse them to your accounts.
4. Use two-factor authentication
Two-factor authentication provides an additional layer of safety to your X account. When you log in, you want to enter each a password and a verification code or use a safety key. This method, solely you can entry your account. To enroll, you want to have a verified electronic mail deal with linked to your account. X makes use of your electronic mail deal with to talk with you and hold your account safe.
Once you activate this characteristic, you want two issues to log in to your account: your password and a secondary verification methodology. You can select from a code, an app affirmation, or a bodily safety key.
5. Require electronic mail and cellphone quantity to request a reset password hyperlink or code
Having an up-to-date electronic mail deal with connected to your account is an effective way to enhance your account safety. Also, including a cellphone quantity to your account is a good step to hold your account safe. With a cellphone quantity in your account, you’ll have the opportunity to enroll in safety features like login verification. It can even permit for quicker account restoration. If you ever lose entry to your account, having a cellphone quantity connected could make it simpler for you to get again into your X account.
6. Be cautious of suspicious hyperlinks
Be cautious of suspicious hyperlinks, and at all times be certain you’re on twitter.com earlier than you enter your login info.
7. Don’t fall for pretend guarantees
Never give your username and password out to third events, particularly these promising to get you followers, make you cash, or confirm you.
8. Make certain your software program is up to date
Make certain your pc software program, together with your browser, is up to date with the latest upgrades and antivirus software program.
9. Have good antivirus software program on all of your units
The finest method to shield your self from having your knowledge breached is to have antivirus safety put in on all of your units. Having good antivirus software program actively operating in your units will alert you of any malware in your system, warn you towards clicking on any malicious hyperlinks in phishing emails, and finally shield you from being hacked. Get my picks for the perfect 2024 antivirus safety winners to your Windows, Mac, Android & iOS units.
10. Check to see in case your account has been compromised
If you actually assume your X account has been hacked, then you ought to examine to see in case your account has been compromised. You can do that by visiting the Security and Login part of your account settings and reviewing the units and places the place you have logged in. If you see any suspicious exercise, equivalent to logins from unknown units or places, you ought to instantly change your password and allow two-factor authentication. You also needs to report any unauthorized entry to X.
If you suspect you’re a sufferer of a social media scammer
If you suspect you’re a sufferer of a social media scammer, you want to take pressing motion instantly. Here are some quick steps to take.
Secure your account
Immediately change your password to lock potential hackers out. If you’re locked out of your account, contact X’s assist instantly to recuperate it.
Inform your contacts
Let your family and friends know in order that they’re conscious. That method, hackers will not dupe them with messages or requests coming out of your compromised account.
Monitor account actions
Keep a watch in your energetic periods, messages despatched, and any modifications made to your account. You ought to attempt to report and reverse any unfamiliar exercise.
Seek skilled assist
If you consider your private info, equivalent to monetary knowledge or different delicate particulars, has been compromised, take into account reaching out to cybersecurity professionals or companies. They can information you on additional restoration and safety steps.
Use id theft safety
If you need a service that may stroll you by each step of the reporting and restoration course of, among the best issues you can do to shield your self from the sort of fraud is to subscribe to an id theft service.
Theft safety corporations can monitor private info like your house title, Social Security quantity, cellphone quantity, and electronic mail deal with. They may also alert you whether it is on sale on the darkish internet or if somebody is utilizing it to open an account. They may also help you in freezing your financial institution and bank card accounts to stop additional unauthorized use by criminals. See my ideas and finest picks on how to shield your self from id theft.
MORE: HOW TO OUTSMART CRIMINAL HACKERS BY LOCKING THEM OUT OF YOUR DIGITAL ACCOUNTS
Kurt’s key takeaways
These hackers are attempting to make the most of your belief and hope you let your guard down. That’s why it is so essential to be vigilant. While they are attempting to idiot you with official-looking accounts, attempt to confirm them utilizing the individual or group’s web site or different social media accounts. While X’s grey and gold verification marks are often reliable, they are not 100% foolproof.
CLICK HERE TO GET THE FOX NEWS APP
What do you assume X or different social media platforms ought to do to stop or cease crypto scams? Let us know by writing us at Cyberguy.com/Contact.
For extra of my tech ideas & safety alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a query or tell us what tales you’d like us to cowl.
Answers to essentially the most requested CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
[ad_2]
Source hyperlink





