[ad_1]
There is sufficient to fear about in life without the extra stress and terror of discovering out your pals, household or full strangers have been receiving a text message from “you” without your data. How did they try this? How did they send a text message from your phone without you knowing?
This is an actual menace that many individuals face on daily basis. That’s why we felt it was so vital to reply this query despatched in from John.
“I just found a text written to me, which was a response to a text I sent. Problem is, I didn’t send the text? I’m 65 years old, and not as spry as I once was, but I do not remember sending the text. My wife is trying to convince me I’m going crazy. She says it’s impossible for someone to send a text (impersonating me) without having possession of my phone. Is that true? Can someone hack your phone and send text??” – John, Fort Myers, FL
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS, AND EASY HOW-TO’S TO MAKE YOU SMARTER
What is SMS spoofing?
We’re sorry to listen to that you’re going by this, John. It is feasible for somebody to send a text message impersonating you without having possession of your phone. This is named SMS spoofing, and it’s a approach utilized by cybercriminals to send fraudulent text messages.
How does SMS spoofing work?
SMS spoofing works by manipulating the sender ID of a text message to make it seem as if it was despatched from a distinct phone quantity. This can be achieved utilizing varied on-line providers that permit customers to send text messages with a pretend sender ID. Cybercriminals will change the sender ID to impersonate pals, household, or a reputable firm.
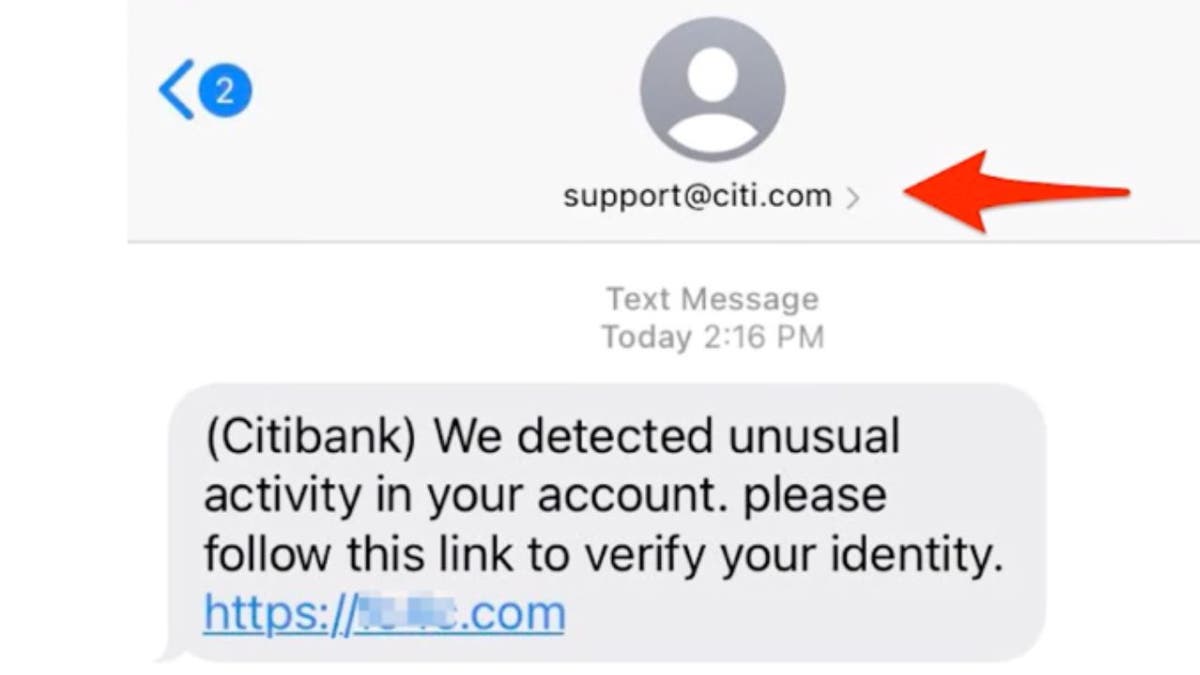
Example of text message screenshot of hacker pretending to be a financial institution (Kurt “CyberGuy” Knutsson)
It is vital to notice that SMS spoofing is unlawful and can be used for malicious functions reminiscent of phishing scams, identification theft, and fraud. Scammers financial institution on the mix of familiarity and urgency to get you to work together with their text both by clicking on a hyperlink, downloading a file, or responding with private data.
How to identify and keep away from SMS spoofing scams
Here are the highest 3 the reason why scammers typically send text messages underneath a pretend sender ID with some pressing request:
1. Trick you into clicking on a malicious hyperlink that leads you to a malicious web site to rob you of your private or monetary data and even unleash malware or viruses to your phone.
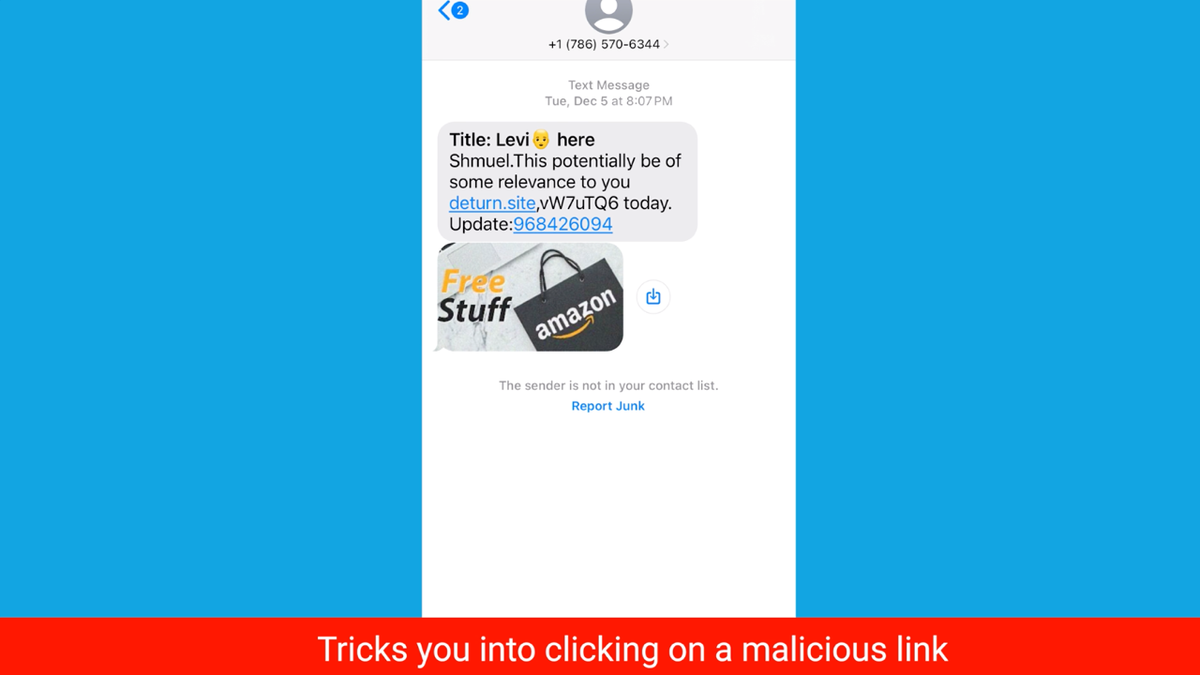
Screenshot of text SMS spoof making an attempt to trick you to click on a malicious hyperlink (Kurt “CyberGuy” Knutsson)
2. Lure you into paying a pretend invoice underneath the guise of a good or acquainted firm.
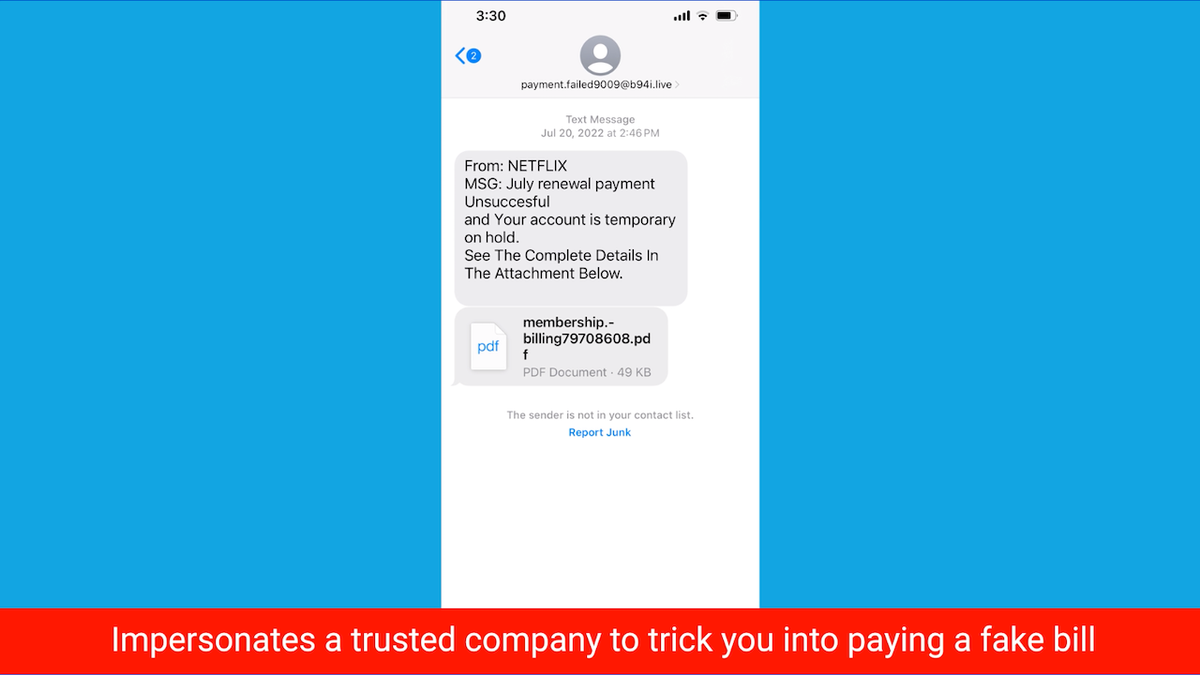
Screenshot of text spoof making an attempt to trick you to pay pretend invoice (Kurt “CyberGuy” Knutsson)
3. Damages your status or relationship with pals, household, and others by sending dangerous messages.
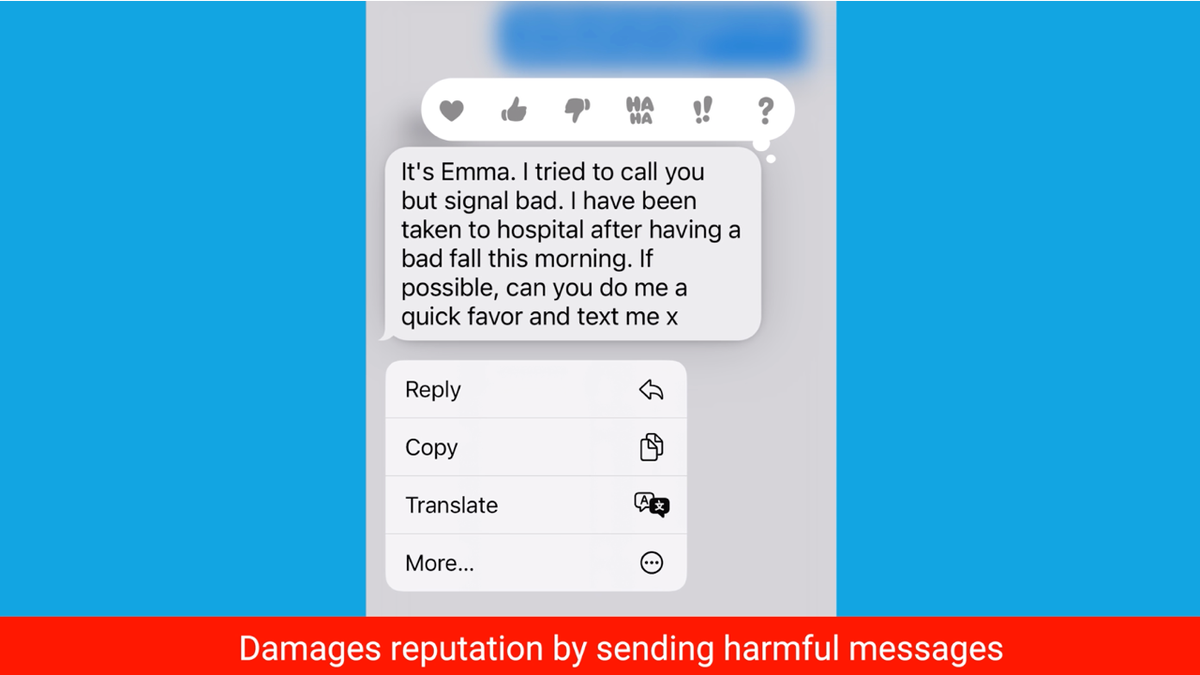
Screenshot of text spoof making an attempt to break your status (Kurt “CyberGuy” Knutsson)
iMessage Vulnerabilities
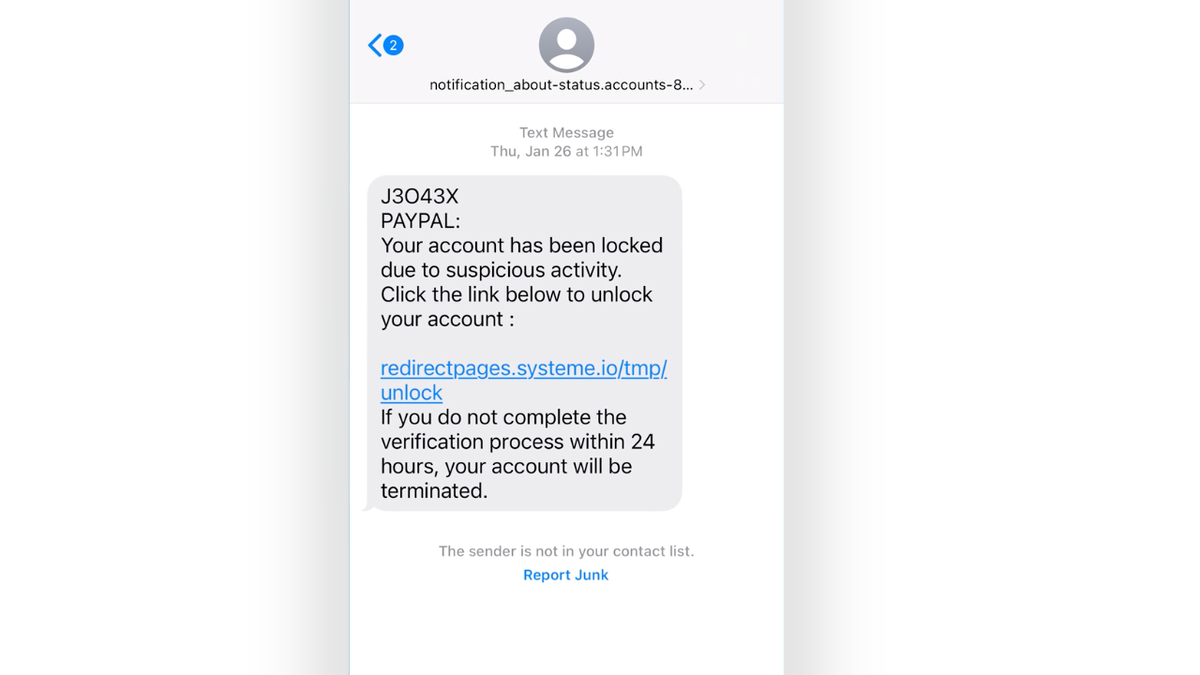
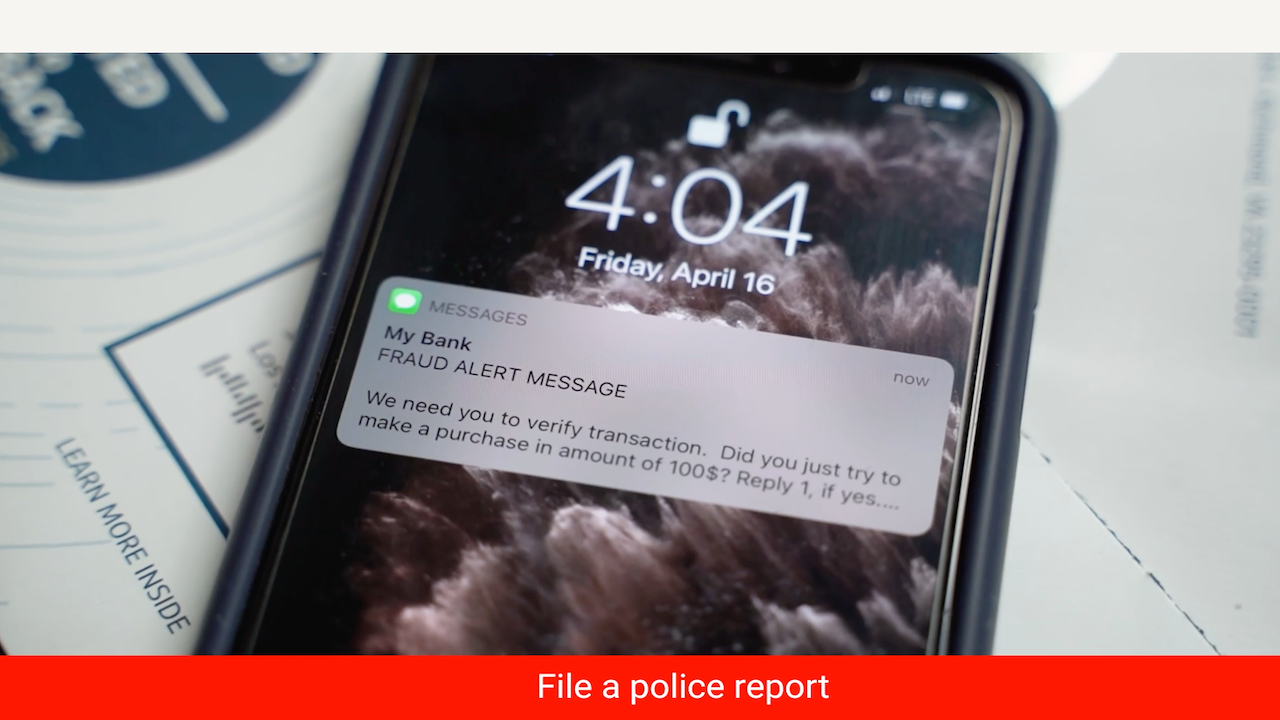
SMS spoof on Apple system from hacker posing as monetary establishment (Kurt “CyberGuy” Knutsson)
In the previous, many Apple units had been thought of to be nearly resistant to viruses and malware. Unfortunately, as a result of bugs in iOS, hackers can take over somebody’s system similar to another system in the marketplace. While Apple patches these vulnerabilities on a constant foundation, this leaves iPhone customers susceptible to SMS spoofing, too.
A hacker can use “interaction-less” bugs to send a specifically crafted SMS message and the iMessage server can send user-specific knowledge, together with photos or SMS messages, again to them. The person doesn’t even should open the messages to activate this bug. Additionally, hackers can send malicious codes by texts, embedding them onto the person’s phone. These vulnerabilities are distinctive to Apple units.
Aside from the particular vulnerabilities, hackers typically want the person to work together with the text message earlier than the malicious code will get unleashed onto the system.
MORE: CHECK AND DETECT IF SOMEONE YOU KNOW IS SNOOPING ON YOUR IPHONE
7 Actions to take if you suspect SMS spoofing
If you suspect that your phone has been hacked or that somebody is impersonating you, it is very important take quick motion. Here are some steps you can take:
1) Have good antivirus software program on your phone: Having good antivirus software program actively working on your units will alert you of any malware in your system, warn you in opposition to clicking on any malicious hyperlinks which will set up malware on your units, permitting hackers to realize entry to your private data. Find my assessment of Best Antivirus Protection right here.
2) Keep your phone software program up to date: Both iPhone and Android customers ought to hold their phone’s OS and apps up to date commonly as Apple and Google launch patches to vulnerabilities as they’re found. Updating your telephones can forestall hackers from exploiting safety flaws and sending text messages from your phone without you knowing.
3) Change your passwords: Change the passwords for all your on-line accounts, together with your e-mail, social media, and banking accounts. Do not use easy-to-guess data reminiscent of your birthday or tackle. Use robust, distinctive passwords which can be tough to guess; ideally ones which can be alphanumeric and, if relevant, embrace particular symbols. Be certain to do that on one other system in case there’s malware on your phone monitoring you. Consider utilizing a password supervisor to generate and retailer advanced passwords. It will assist you to create distinctive and difficult-to-crack passwords {that a} hacker may by no means guess.
4) Enable two-factor authentication: Enabling two-factor authentication on all your on-line accounts will add an additional layer of safety to your accounts and make it harder for hackers to realize entry.
5) Contact your cellular service: Contact your cellular service and report the incident. They could possibly assist you determine the supply of the text message and take applicable motion.
6) File a police report: If you consider that you have been a sufferer of identification theft or fraud, file a police report with your native legislation enforcement company.
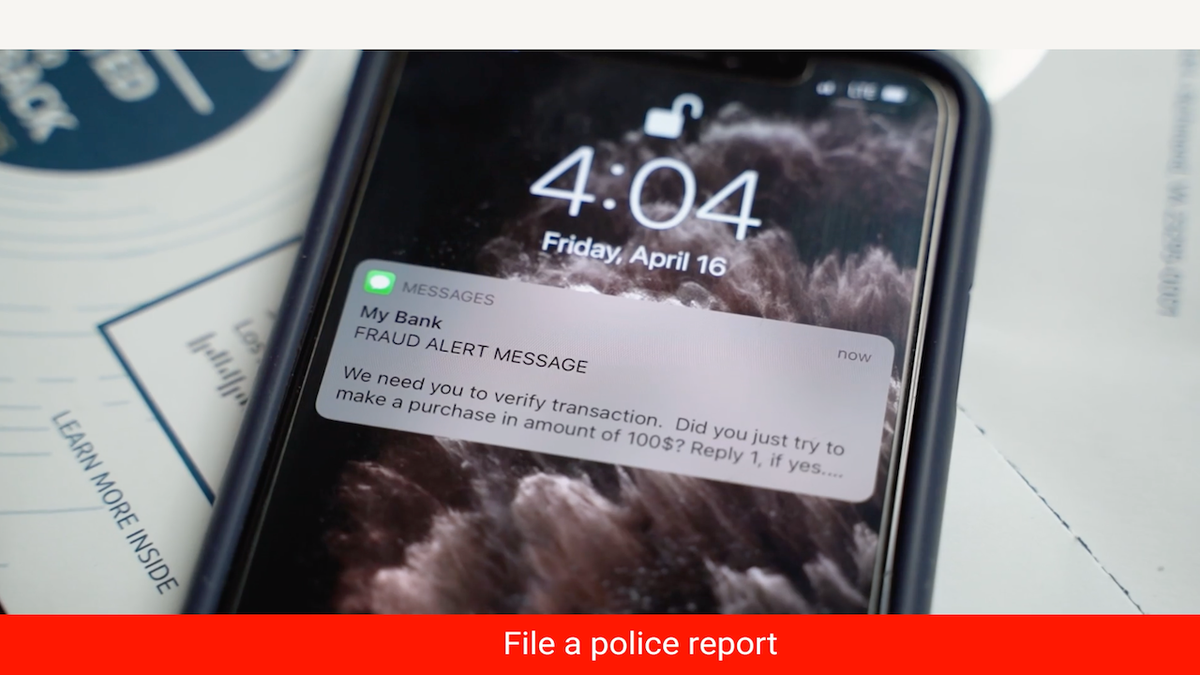
Fraud detection text message alert on iPhone (Kurt “CyberGuy” Knutsson)
7) Watch your connections: When doable, don’t hook up with unprotected or public Wi-Fi hotspots or Bluetooth connections. Turn off the Bluetooth connection when not in use. On most iPhones, you can select who to obtain recordsdata or photographs through AirDrop (a Bluetooth characteristic) from by deciding on to obtain from “no one,” folks in your Contacts, or Everyone. We counsel you set it to “no one” and solely flip it on when you are with the individual you are sending or receiving a file or photograph from.
MORE: GUARD YOUR PASSWORDS: CHERRYBLOS; FAKETRADE MALWARE THREATEN ANDROIDS
I’ve been scammed by SMS spoofing. What to do subsequent?
Below are some subsequent steps if you discover you or your beloved one is a sufferer of identification theft from an SMS spoofing assault.
1) Change your passwords. If you suspect that your phone has been hacked or that somebody is impersonating you, they might entry your on-line accounts and steal your knowledge or cash. ON ANOTHER DEVICE (i.e., your laptop computer or desktop), you ought to change your passwords for all your vital accounts, reminiscent of e-mail, banking, social media, and many others. You wish to do that on one other system so the hacker isn’t’ recording you organising your new password on your hacked system. Use robust and distinctive passwords which can be onerous to guess or crack. You can additionally think about using a password supervisor to generate and retailer your passwords securely.
2) Look by financial institution statements and verify account transactions to see the place outlier exercise began.
3) Use a fraud safety service. Identity Theft corporations can monitor private data like your Social Security Number (SSN), phone quantity, and e-mail tackle and alert you whether it is being bought on the darkish net or getting used to open an account. They can additionally help you in freezing your financial institution and bank card accounts to stop additional unauthorized use by criminals.
Some of one of the best components of utilizing an identification theft safety service embrace identification theft insurance coverage to cowl losses and authorized charges and a white glove fraud decision workforce the place a U.S.-based case supervisor helps you get better any losses. See my suggestions and greatest picks on the best way to shield your self from identification theft.
4) Report any breaches to official authorities businesses just like the Federal Communications Commission.
5) You could want to get the skilled recommendation of a lawyer earlier than chatting with legislation enforcement, particularly when you are coping with felony identification theft, and if being a sufferer of felony identification theft leaves you unable to safe employment or housing
6) Alert all three main credit score bureaus and presumably place a fraud alert on your credit score report.
7) Run your personal background verify or request a duplicate of 1 if that’s how you found your data has been utilized by a felony.
8) Alert your contacts. If hackers have accessed your system by SMS spoofing, they might use it to send spam or phishing messages to your contacts. They may impersonate you and ask for cash or private data. You ought to alert your contacts and warn them to not open or reply to any messages from you that appear suspicious or uncommon.
9) Restore your system to manufacturing facility settings. If you wish to be sure that your system is totally freed from any malware or spyware and adware, you can restore it to manufacturing facility settings. This will erase all your knowledge and settings and reinstall the unique model. You ought to again up your vital knowledge BEFORE doing this, and solely restore it from a trusted supply.
If you are a sufferer of identification theft, crucial factor to do is to take quick motion to mitigate the injury and forestall additional hurt.
MORE: HOW TO TELL IF SOMEONE HAS READ YOUR TEXT MESSAGE
Kurt’s key takeaways
It’s doable for somebody who doesn’t have bodily possession of your phone to spoof your data for SMS spoofing. Though you won’t have management over who will get your quantity, there are steps you can take to guard your self.
Have you ever acquired a convincing text spoof message? What had been the telltale indicators that it was a spoofed message? Let us know by writing us at Cyberguy.com/Contact.
For extra of my tech suggestions & safety alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a query or tell us what tales you’d like us to cowl.
Answers to essentially the most requested CyberGuy questions:
Ideas for utilizing these Holiday Gift playing cards
Copyright 2024 CyberGuy.com. All rights reserved.
[ad_2]
Source hyperlink