[ad_1]
If you use a Mac, it might be in danger of two new threats. While Apple has a status for having ironclad safety, these two items of malware are designed to trick you and steal your knowledge.
Jamf Threat Labs, a corporation that focuses on the security of Apple merchandise, says the malware threats are half of a year-long assault on Mac methods.
The group says hackers are utilizing them to reap knowledge. Attacks like these are continually occurring, in response to the lab. That makes it all of the extra vital for those who use a Mac to make sure your knowledge is locked down.
It’s vital to notice that, in response to the lab, these hackers largely goal the crypto business, placing those people, notably, in danger. That mentioned, all Mac customers ought to nonetheless train warning.

MacGuide Pro (Kurt “CyberGuy” Knutsson)
Malware posing as advertisements
Before we get into the malware, let’s discuss Arc Browser. For those unfamiliar with it, Arc Browser is a Mac internet browser that appears to present customers a singular expertise. First and foremost, the primary focus is on the webpage. Any buttons you may discover in a conventional browser are relegated to a sidebar. It makes use of a bookmark system that offers you a number of workspaces. It additionally has automated tab administration.
In different phrases, many Mac customers would contemplate Arc Browser an improve over the already-included Safari. And its ever-growing reputation makes it an enormous goal for hackers.
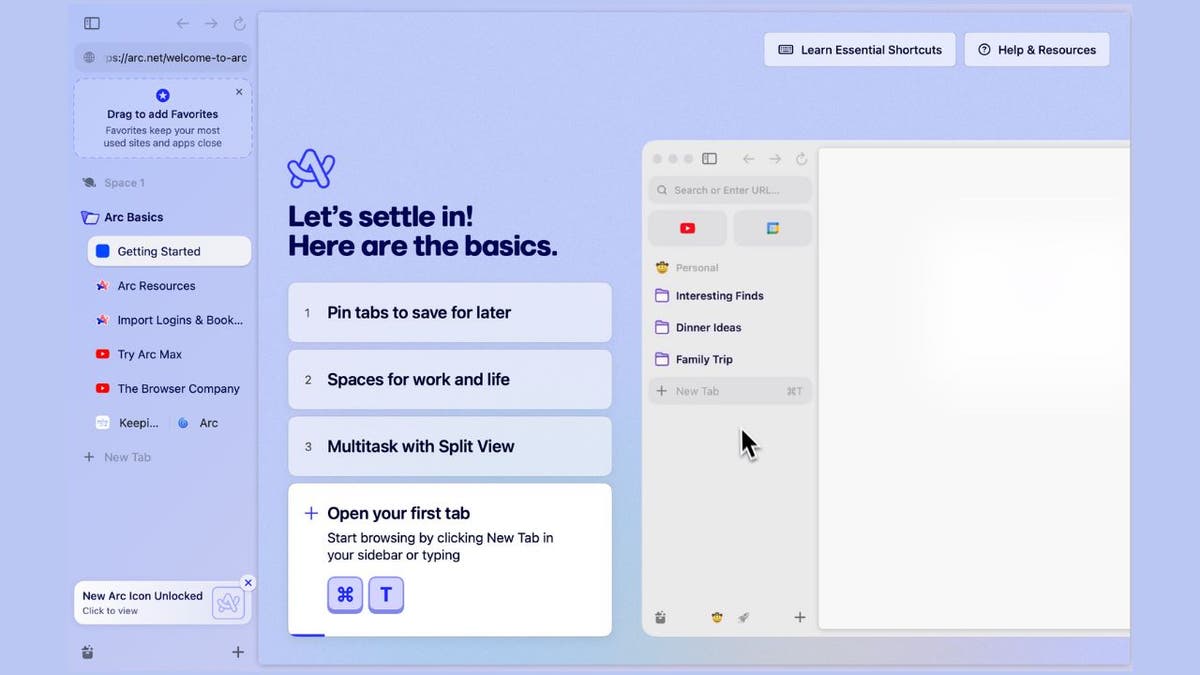
Legitimate Arc Browser web site (Kurt “CyberGuy” Knutsson)
MORE: HOW CRYPTO IMPOSTERS ARE USING CALENDY TO INFECT MACS WITH MALWARE
How faux Arc Web Browser advertisements conceal harmful malware
In this assault, hackers are hiding malware in ads posing as advertisements for Arc Browser, as seen under.
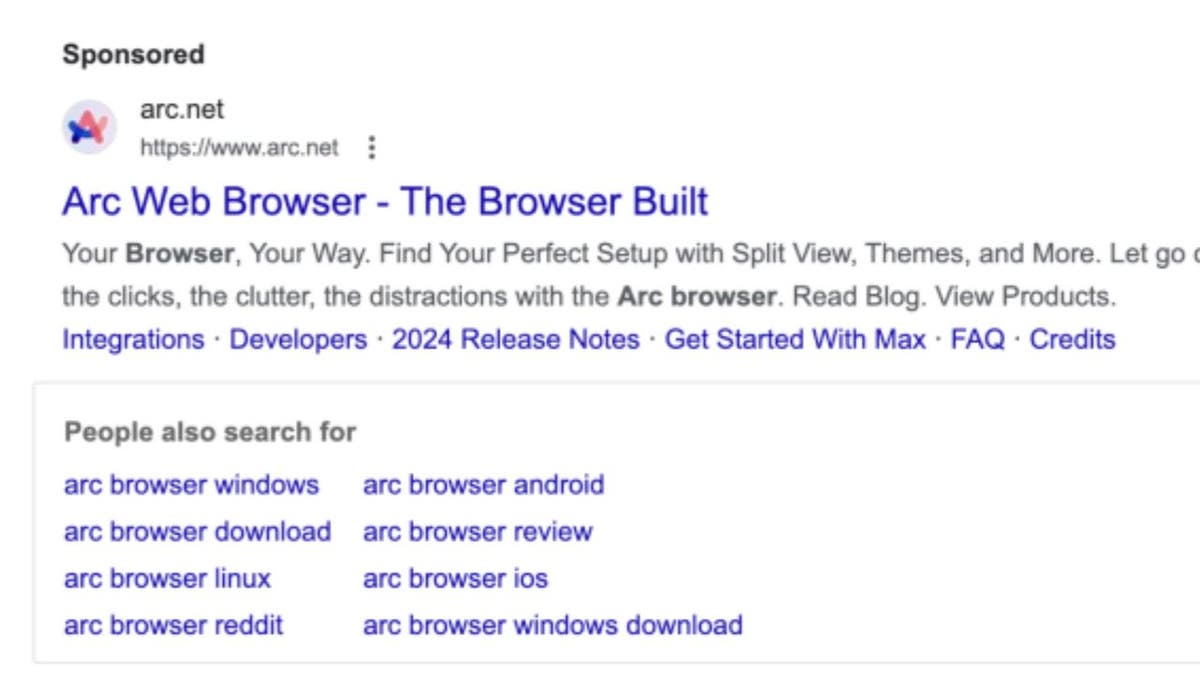
Malicious website aricl[.]internet that imitates the reliable arc.internet (Jamf Threat Labs)
The advert redirects to a malicious lookalike website: arc.internet vs. aricl.internet
Instead of taking you to the reliable obtain web page for the Arc internet browser, the advert takes you to a lookalike malicious website, aricl[.]internet, that imitates the reliable arc.internet and hosts malware.
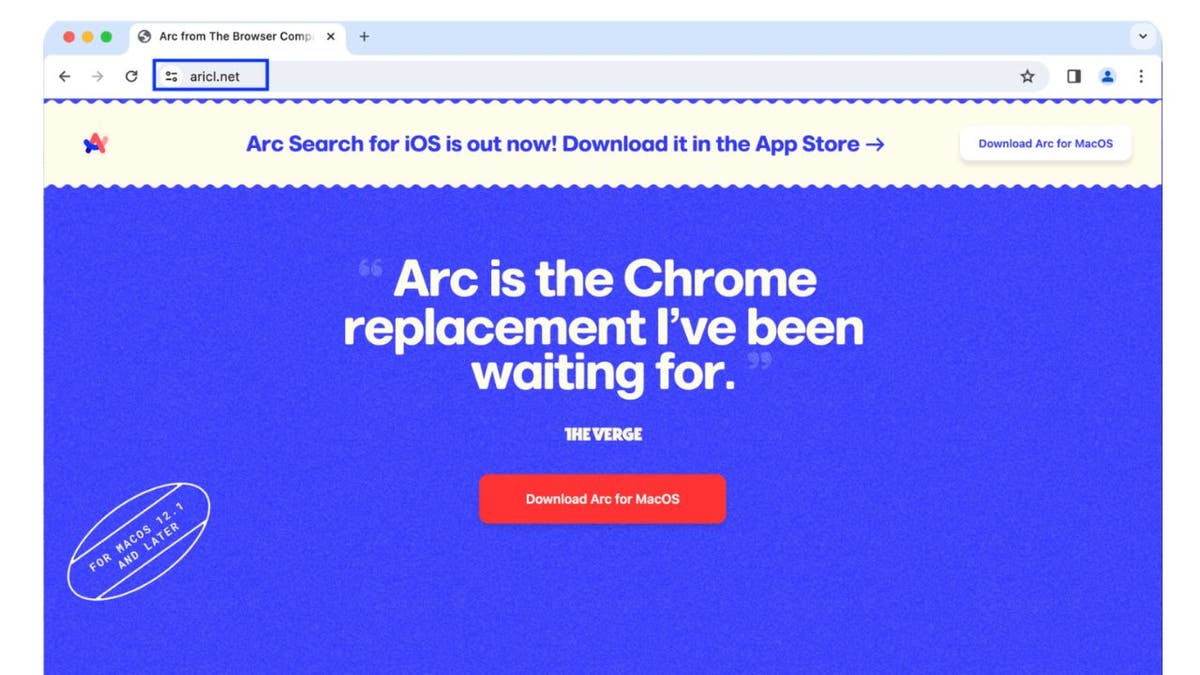
Image of the malicious aricl[.]internet website (Jamf Threat Labs)
Malware disguised as Arc Browser unleashes Atomic Stealer
Once you obtain malware posing as Arc Browser, the malware unleashes an Atomic stealer. It’s a faux immediate that appears like a traditional System Preferences immediate asking you to your password. Once the hackers get entry to your system password, they will steal different knowledge.
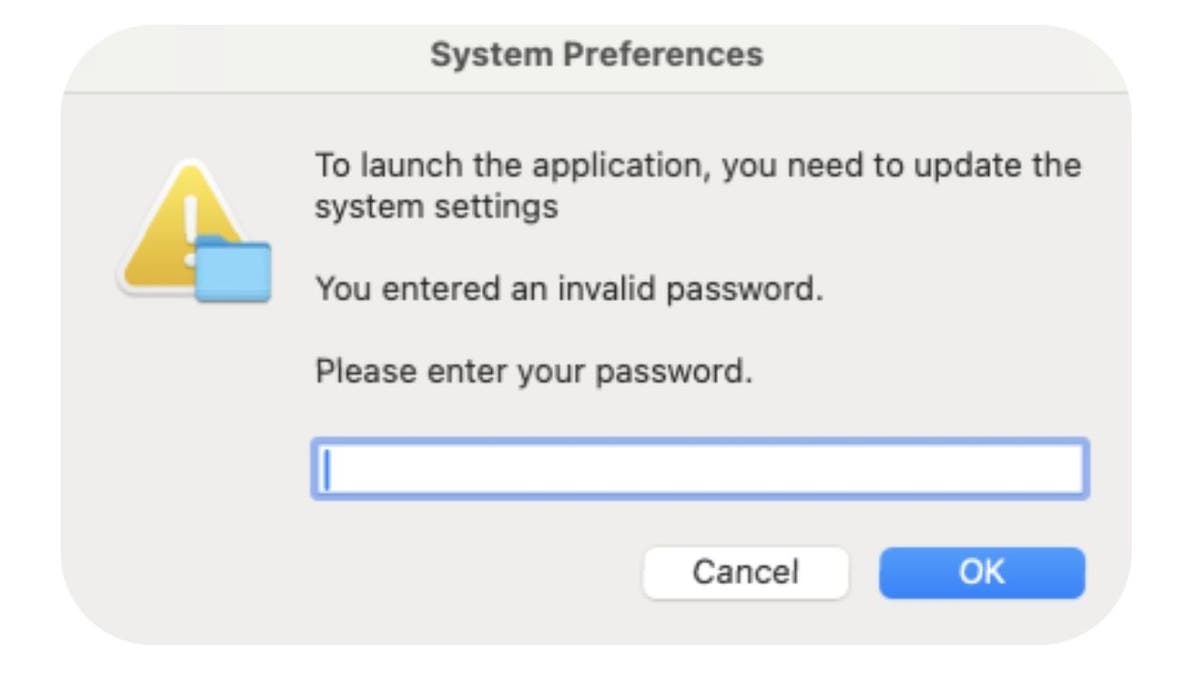
Fake system preferences immediate (Jamf Threat Labs)
Even worse, these so-called “ads” can seem as sponsored ads in a Google search. Jamf Threat Labs says these hyperlinks can solely be accessed by way of a generated sponsored hyperlink and never accessed straight. Attempts to entry the malicious web site straight returned an error message. This is presumably completed to evade detection.
Fake assembly software program
The researchers at Jamf Threat Labs have additionally found a faux web site that gives malware hidden as free group assembly scheduling software program. Meethub[.]gg seems to be reliable. The firm posts articles on Medium and has greater than 8,000 followers on X, on the time of publishing. It, nevertheless, hosts malware that is associated to Realst, one other piece of malware designed to empty crypto wallets.
Some of the assaults involving Meethub use social engineering. A hacker may strategy their sufferer trying to interview them for a job or a podcast. In order to satisfy, they ask the sufferer to obtain Meethub’s software program. According to Jamf, these assaults can typically result in massive paydays for hackers.
Meethub web site (Jamf Threat Labs)
How to guard your self
1. Don’t obtain bootleg software program: It’s not well worth the danger to obtain bootleg software program. It exposes your machine to potential safety threats like viruses and spy ware. If somebody emails you a hyperlink for a obtain, be certain it’s from a good supply and scan it.
2. Don’t click on on suspicious hyperlinks or information: If you encounter a hyperlink that appears suspicious, misspelled or unfamiliar, keep away from clicking on it. Instead, contemplate going on to the corporate’s web site by manually typing within the internet deal with or trying to find it in a trusted search engine. Most usually, the first or second consequence that comes up is reliable. If you see the phrase “Sponsored “above the search consequence, take a beat earlier than clicking it and contemplate clicking on the consequence under it.
3. Have good antivirus software program: The finest option to defend your self from clicking malicious hyperlinks that set up malware which will get entry to your personal data is to have antivirus safety put in on all of your gadgets. This may alert you of any phishing emails or ransomware scams. Get my picks for one of the best 2024 antivirus safety winners to your Mac, Windows, Android & iOS gadgets.
MORE: STEALTHY BACKDOOR MAC MALWARE THAT CAN WIPE OUT YOUR FILES
What to do if you’ve been hacked
If it has already occurred, and you’ve been hacked, then you ought to take rapid motion to reduce the harm and safe your machine. Here are some steps that you can comply with:
Change your passwords
If hackers have recorded your passwords, they may entry your on-line accounts and steal your knowledge or cash. On one other machine (i.e., your laptop computer or desktop), you ought to change your passwords for all of your vital accounts, comparable to e-mail, banking, social media, and so on. You wish to do that on one other machine so the hacker isn’t recording you organising your new password in your hacked machine. And you also needs to use robust and distinctive passwords that are exhausting to guess or crack. You may use a password supervisor to generate and retailer your passwords securely.
Enable two-factor authentication
You’ll wish to activate two-factor authentication for an additional layer of safety.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
Monitor your accounts and transactions
You ought to test your on-line accounts and transactions repeatedly for any suspicious or unauthorized exercise. If you discover something uncommon, report it to the service supplier or authorities instantly. You also needs to assessment your credit score studies and scores to see if there are any indicators of identification theft or fraud.
Use identification theft safety
Identity theft safety firms can monitor private data like your private home title, Social Security quantity, cellphone quantity and e-mail deal with and alert you whether it is getting used to open an account. They may help you in freezing your financial institution and bank card accounts to stop additional unauthorized use by criminals. See my suggestions and finest picks on how you can defend your self from identification theft.
Contact your financial institution and bank card firms
If hackers have obtained your financial institution or bank card data, they may use it to make purchases or withdrawals with out your consent. You ought to inform your financial institution and bank card firms of the state of affairs. They can assist you freeze or cancel your playing cards, dispute any fraudulent expenses, and problem new playing cards for you.
Alert your contacts
If hackers have accessed your e-mail or social media accounts, they may use them to ship spam or phishing messages to your contacts. They might additionally impersonate you and ask for cash or private data. You ought to alert your contacts and warn them to not open or reply to any messages from you that appear suspicious or uncommon.
MORE: HOW A FLEW IN iPHONE’S SECURITY COULD LEAVE YOU LOCKED OUT
Kurt’s key takeaways
While Macs are typically safe gadgets, that hasn’t stopped hackers from stealing knowledge. In reality, these two new assaults present how inventive they are often whereas attempting to interrupt into your machine. That’s why it is so vital to have good antivirus software program and security practices.
Good security practices are much more important for folks who commerce and use cryptocurrencies in these explicit conditions. As talked about earlier than, these assaults focus largely on draining crypto wallets. And whereas anybody may be hacked, crypto customers have a better danger. So take the time to evaluate a hyperlink earlier than clicking on it. Don’t simply obtain software program as a result of somebody tells you to. Do your analysis. At the top of the day, it’s going to assist preserve your knowledge and your pockets protected.
CLICK HERE TO GET THE FOX NEWS APP
Are you anxious about hackers discovering extra inventive methods to interrupt into your laptop? If you use crypto, how are you protecting your crypto pockets protected? Let us know by writing us at Cyberguy.com/Contact
For extra of my tech suggestions and safety alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a query or tell us what tales you’d like us to cowl
Answers to essentially the most requested CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
[ad_2]
Source hyperlink





