[ad_1]
A brand new hacking risk is focusing on crypto customers through Calendly, a preferred meeting-scheduling app. This is a critical challenge that would compromise your safety and privateness, so that you want to concentrate on the way it works and the way to shield your self.
Calendly app (Calendly) (Kurt “CyberGuy” Knutsson)
Hackers are posing as crypto buyers through Calendly
The manner this explicit risk works is fairly easy, but sneaky. To begin, many individuals within the crypto world are looking for investments to help their crypto start-up concepts or one thing associated.
People like this want to be lively in crypto communities and funding areas to join with the correct folks to help them. It’s not unusual for these folks to have a hyperlink to schedule a gathering with them on their profile, through Calendly, a preferred scheduling app not only for folks in cryptocurrency however for anybody.
Calendly app (Calendly) (Kurt “CyberGuy” Knutsson)
How the hacker infiltrates the goal’s machine
Unbeknownst to the soon-to-be sufferer, these hackers are profiting from these people by posing as crypto buyers, the precise form of folks these of us need to get in contact with. When they e book a gathering on this particular person’s calendar, they add a gathering hyperlink that runs a script that installs malware on macOS techniques.
An actual-life instance of how crypto impersonators lure victims
This occurred to one unfortunate particular person on this state of affairs. The hacker reached out through Telegram – an encrypted messaging app – and requested about reserving a gathering. The particular person despatched the “investor” their Calendly hyperlink, and on the day of the assembly, went to the assembly hyperlink that the “investor” had added. In most circumstances, that is regular – a hyperlink to a Zoom or Google Meet just isn’t uncommon. And as a result of the person had already spoken to the particular person through Telegram and appeared respectable, there was no purpose to assume twice about this.
The sinister scheme was revealed when hyperlinks failed
Only when the particular person went to click on the hyperlink and when the “investor” did not present up, did he contact him on the identical Telegram thread. The “investor” apologized for the inconvenience and despatched a brand new hyperlink, explaining there was a difficulty with IT.
However, the hyperlink nonetheless didn’t work, and the assembly by no means occurred, with the “investor” asking to reschedule. It dawned on the particular person a bit of afterward that this may occasionally have been a hack assault, through an Apple Script (file extension “.scpt”) that downloads and executes a malicious Trojan made to run on macOS techniques.
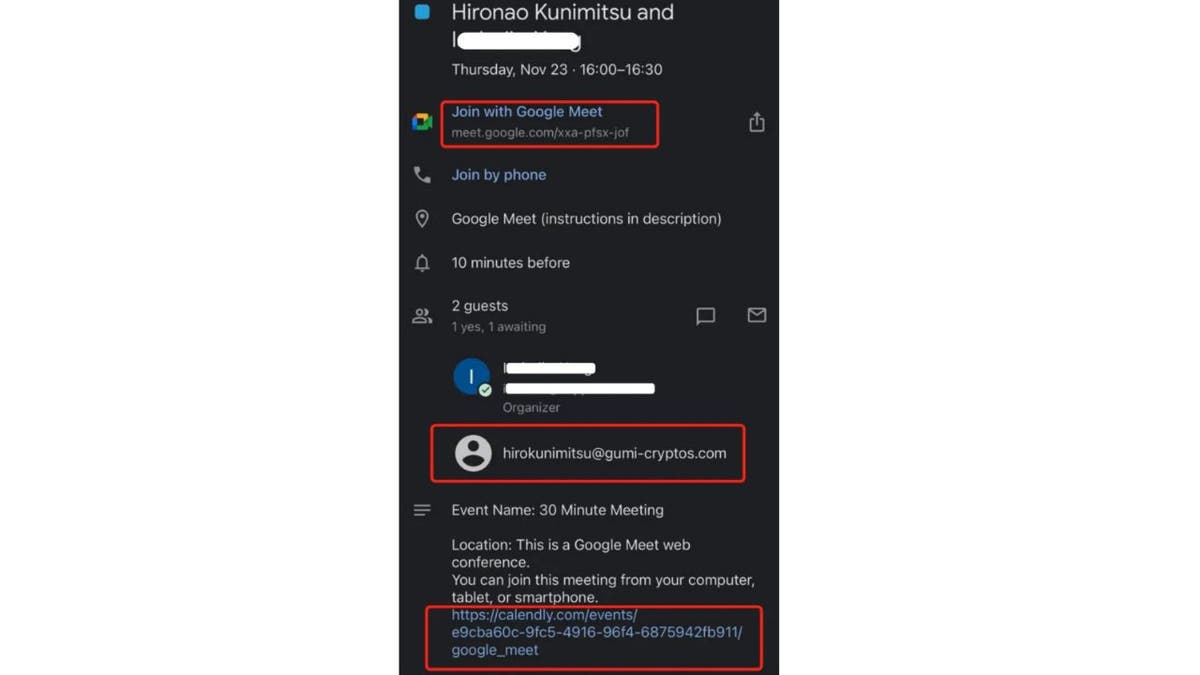
Hacker Google Meet request (SlowMist) (Kurt “CyberGuy” Knutsson)
MORE: STEALTHY BACKDOOR MAC MALWARE THAT CAN WIPE OUT YOUR FILES
How fast motion foiled a Mac malware assault
Because the one that was the goal of this assault promptly backed up their information upon realizing the assault, it prevented the lack of proof relating to the precise malware downloaded onto their macOS. Cybersecurity companies had been ready to analyze the script info, which led them to establish similarities with earlier assaults carried out by the identical group and warn the general public.
Security alert (SlowMist) (Kurt “CyberGuy” Knutsson)
MORE: HOW TO PROTECT YOUR MAC FROM THE NEW METASTEALER MALWARE
The perpetrators are a hacker group from North Korea
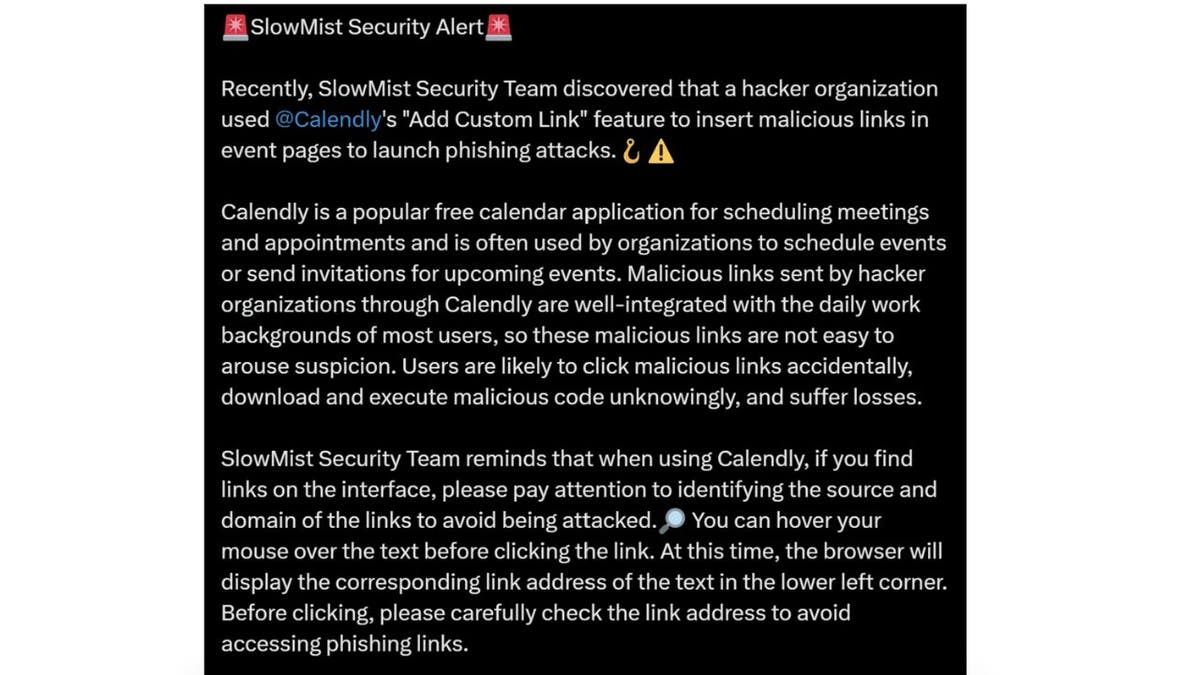
A cybersecurity agency found a phishing assault in 2023 that was carried out by state-sponsored hackers from North Korea, particularly a subgroup of the infamous Lazarus group. This group sometimes targets monetary good points, aiming to steal cash or cryptocurrency to fund the North Korean army regime.
In this explicit assault, the North Korean hackers exploited the “Add Custom Link” characteristic inside the Calendly assembly scheduling system on occasion pages to insert malicious hyperlinks and provoke phishing assaults. They additionally make use of related techniques on Telegram.
This incident underscores the significance of vigilance and strong safety measures to safeguard towards cyberthreats, particularly these originating from state-sponsored actors.
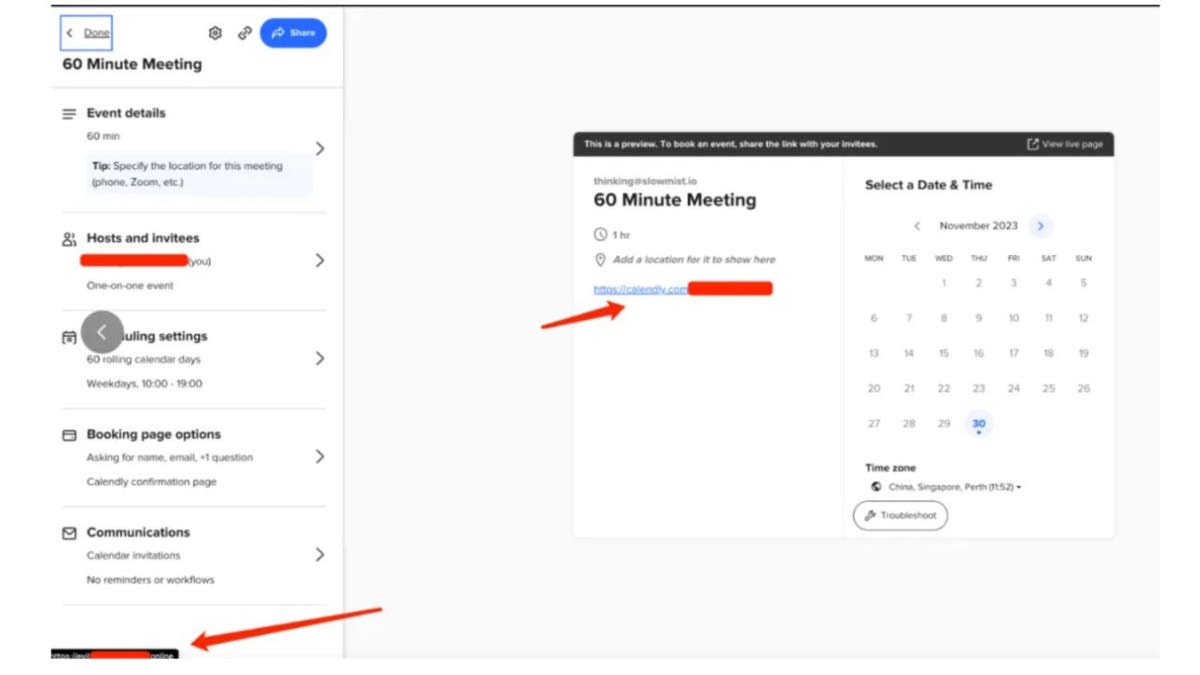
Add Custom Link characteristic (SlowMist) (Kurt “CyberGuy” Knutsson)
Calendly’s response to malware assaults
We reached out to Calendly, and their CISO (chief info safety officer), Frank Russo, supplied us with this assertion.
“We’re aware of these types of social engineering attacks by cryptocurrency hackers. This attack violates our Terms of Use, and accounts are immediately terminated when discovered or reported. To help prevent these kinds of attacks, our security team and partners have implemented a service to automatically detect fraud and impersonations that could lead to social engineering. We are also actively scanning content for all our customers to catch these types of malicious links and to prevent hackers earlier on. Additionally, we intend to add an interstitial page warning users before they’re redirected away from Calendly to other websites.”
How to shield your self towards cyberthreats
MacOS customers have a tendency to expertise fewer malware assaults than PC customers. But this concept could make MacOS customers extra weak to assaults as a result of they might really feel they are merely protected. Because hackers are getting an increasing number of refined, it is essential by no means to let your guard down and to observe these precautions.
Be cautious with hyperlinks: If you obtain a Calendly hyperlink from an unfamiliar sender, chorus from clicking on any embedded hyperlinks, even when the sender seems reliable. Additionally, train vigilance when dealing with phishing emails or messages associated to crypto exchanges or wallets, as they might comprise malicious attachments or hyperlinks with malware. When using Calendly, be aware of the supply and area of any hyperlinks you encounter on the interface. Before clicking, hover your mouse over the textual content to confirm the hyperlink tackle and keep away from accessing doubtlessly dangerous phishing hyperlinks.
Send assembly hyperlinks your self: Whenever potential, ship the assembly hyperlink straight to the particular person scheduling the decision. This minimizes the chance of by chance clicking on malicious hyperlinks.
Have good antivirus software program: The finest manner to shield your self from clicking malicious hyperlinks that set up malware that will get entry to your non-public info is to have antivirus safety put in on all of your gadgets. This also can provide you with a warning of any phishing emails or ransomware scams. Get my picks for the perfect 2024 antivirus safety winners in your Mac, Windows, Android & iOS gadgets.
Perform common updates: Regularly replace your working system and safety software program to keep forward of potential vulnerabilities.
Have sturdy passwords and use two-factor authentication: Using the identical password throughout a number of platforms will all the time make you extra weak as a result of if one account will get hacked, all of them get hacked. And two-factor authentication is simply an additional defend that may forestall a hacker from stepping into your accounts. Make positive to use a password supervisor to hold observe of all of your passwords.

Person typing on a laptop computer (Kurt “CyberGuy” Knutsson)
MORE: DON’T FALL FOR THESE SNEAKY TAX SCAMS THAT ARE OUT TO STEAL YOUR IDENTITY AND MONEY
Kurt’s key takeaways
As lengthy as there’s cash and data to steal on-line, hackers will cease at nothing to trick harmless folks into downloading malware onto their gadgets. So, keep up to date with the newest threats so as to make sure you’re doing every little thing to shield your self.
Have you encountered suspicious assembly requests through Calendly or different scheduling apps? Do you assume the app firms ought to do extra to confirm the authenticity of such hyperlinks? Let us know by writing us at Cyberguy.com/Contact.
For extra of my tech ideas & safety alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a query or tell us what tales you would like us to cowl.
Answers to probably the most requested CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
[ad_2]
Source hyperlink